VPN is an abbreviation of Virtual Private Network, which is a technology that protects against monitoring, blocking, hacking, censorship, etc. on the Internet and also makes the user anonymous.
VPN secures the Internet connection with encryption that rewrites the data stream so that it becomes unreadable and unusable for unauthorized persons. It prevents monitoring of the user's activity on the web and protects against censorship by preventing the blocking of websites etc.
In addition, the IP address is hidden by using one VPNserver as an intermediary between the user and the rest of the network. It provides anonymity as the IP address can be used for tracking and identification. VPN also provides access to a more free internet as it can be used to bypass blocking by acting as a virtual location.

When you're done here, you'll most likely want to know more about VPN or have help choosing one VPN-favor. A little further down the page you can read more about how VPN works, some typical situations it can be used in and how to get started.
If you are looking for a good one VPNservice, is here reviews of more than 20, where they are thoroughly checked in the seams. Here we read the fine print in the terms of use, check download speeds and many other things that are important in order to VPN works optimally. If you're only interested in the best of them, this list is included the 5 best VPNservices maybe interesting.
Top 5 VPN services
provider | Score | Price (from) | Review | website |
10/10 | Kr. 47 / md | |||
10/10 | Kr. 42 / md
| |||
9,8/10 | Kr. 44 / md
| |||
9,7/10 | Kr. 35 / md
| |||
9,7/10 | Kr. 36 / md
|
Table of Contents:
- How works VPN?
- What is used VPN to?
- Avoid registration and monitoring
- Use the web anonymously
- Access blocked services and websites
- Use public Wifi and other open networks securely
- Avoid censorship and use the web freely
- VPN does not protect against everything
- Disadvantages of using VPN
- Which one VPNservice is best?
- Is secure encryption used?
- Privacy and anonymity on the web
- server Locations
- Network Speed
- additional Features
- Other things worth considering
- Prices and subscriptions
- Can you get VPN free?
- Get started VPN
What is VPN and how does it work?
The Internet is a worldwide network of devices such as. PCs, smartphones, web servers, routers and more. The devices can communicate with each other via wireless and wired connections by exchanging data packets, which contains some form of information.
As a starting point, the information is not encrypted, but is sent as is plain text, which can be read by anyone who gets hold of the data packets. It has the great advantage that exchanging information is easy if all devices can easily read each other's data.
However, there is also a major drawback; namely that information can end up in the wrong hands. Without encryption, one's payment information, passwords and other sensitive information could be intercepted by unauthorized persons and misused.
This happens e.g. by Evil Twin attack, which aims to get people to connect to fake Wi-Fi hotspots controlled by the attacker, who can thereby intercept data. Evil Twin attacks are usually carried out in hotels, coffee shops, educational institutions and other public places where many indiscriminately use the freely available Internet.
VPN secures the internet connection with encryption
VPN generally works by creating an encrypted connection between the user's device and a VPNserver. The server then acts as a link to the rest of the Internet, through which all data to and from the user passes.
Encryption rewrites the contents of the data packets to ciphertext, which can only be decoded by the device and the server. VPN- the client on the user's device decrypts data so that it is readable by various programs or apps and does the same VPN-server, so that data can be read by the devices that are communicated with.
The figure here illustrates the principle:

If someone or something manages to intercept the data packets exchanged between the device and the server, they cannot be used for anything, as the encryption has rendered them unreadable and useless. It protects sensitive data from falling into the wrong hands, but VPN indirectly provides a number of other benefits:
- The encryption makes it impossible to monitor the data traffic and use the information to record the user's movements on the web. In addition to securing payment information etc., it also hides which websites etc. are visited.
- Censorship in the form of blocking access to certain places on the web can also often be avoided VPN- connection that acts as a "tunnel" through the technical measures that limit access.
- The user's IP address is also hidden from the rest of the Internet, which can only "see" VPNserver IP address. It prevents tracking of the user, which provides anonymity online, and can also be used to access blocked sites.
Uden VPN the data stream is basically not encrypted and can therefore be monitored by e.g. Internet Service Provider (ISP), hackers, etc. Unauthorized persons can thus follow everything you do and intercept personal information as well as exercise censorship by blocking the free use of the Internet.
In addition, the user's own IP address is displayed, which can be used for tracking, blocking of content, etc.
What is encryption?
Encryption is the rewriting of data so that it does not immediately contain usable information and therefore cannot be used for anything. The rewriting is done using an algorithm that uses one encryption key, which is based on some cunning mathematics.
A simple example of text encryption is that letters are rewritten down their position in the alphabet. In this case, the encryption key is A = 1, B = 2, C = 3, etc. The word “monkey” is encrypted with “1 2 5 11 1 20” with this encryption key.
Such a banal encryption key would quickly be decrypted - especially with a computer to help. Hence the type of encryption VPN uses much more advanced and in practice completely impossible to break.
Therefore, only devices that have the encryption key are able to decrypt the encrypted data so that they can be used for something again. In a VPNconnection it is only VPNclient on the user's device and the active one VPNserver that has the encryption key.
How to use VPN?
It may immediately sound awkward to use VPN, for how to connect your device to the server and how to encrypt the connection?
Fortunately, that is not the case. On the contrary, it's hugely easy thanks to VPNthe services' usually very user-friendly software.
In practice, one uses VPN via an application or app on your device - a VPN-client. The client both connects to the server and encrypts and decrypts data.
Everything is done more or less automatically and you basically have to do nothing but choose the server you want to connect to. Often you can even set the client to automatically connect to a server when booting the device, so you always protect your connection.
The client gets from it VPNservice you use, and there are basically clients for all devices. So whether you use a PC, smartphone or tablet, whether the operating system is Windows, MacOS, Android, iOS, Linux or something completely different - then there is (usually) a client for the device / operating system.
The picture below shows ExpressVPNs Windows client, where you connect to a server in New York, USA with a single tap. If you want to connect to another location, just tap on the three dots and select from the list that appears.
Another option is to use one VPN-router, which is basically an ordinary. router connected to a VPNserver. With this solution, all devices on the home network are protected - also devices such as Apple TV, smart TV, etc., which you can not install a VPNclient on.
Er VPN legally?
In free countries there are (yet) no laws prohibiting the encryption of your internet connection.
Therefore, it is 100% legal to use one VPNconnection in Denmark!
However, this is not the case everywhere. In a number of countries such as China, Iran, Russia and more, the state is trying to control citizens' access to the Internet. Pga. the freedom and anonymity VPN provides, the technology is therefore prohibited.
Although using VPN, downloads of pirated films and the like. illegal. You are still subject to the law of the country you are in, even if you are connected to a server elsewhere.

Streaming with VPN is also legal
Do you see Netflix USA in Denmark or Danish TV from abroad, may be in violation of the Terms of Use. However, this is not the same as being illegal. Illegality requires breaches of the country's laws and it is not - only breaches of terms of use.
This can in principle have consequences such as blocking or closing your account. It exists as far as is known not a single example of should ever have happened, but now you are warned.
What is used VPN to?
Someone might be wondering what law-abiding citizens need an encrypted internet connection for? After all, it may immediately sound like something reserved for people who have something to hide. However, there are many situations where ordinary people benefit from one VPN-connection.
Generally gives VPN a secure, anonymous and free internet in an easy and legal way. Whether you want access to blocked streaming services, will surf without censorship, download files, etc. anonymously or in principle just think you have the right to a privacy online.
The 5 most common reasons to use VPN is:
- Avoid registration and monitoring
- Use the web anonymously
- Access blocked services and websites
- Use public Wifi and other open networks securely
- Avoid censorship and use the web freely
Avoid registration and monitoring
If someone tries to monitor the encrypted data traffic between the user's devices and VPNserver, it will therefore appear to the monitor as a "junk" and be completely useless. In practice, therefore, it is impossible to register and monitor what a person is protected by one VPNconnection, doing online.
The technology is extremely secure and is used i.a. of the military, private companies and national intelligence services to protect confidential information. Even with modern supercomputers, breaking the encryption will take many times the life of the universe. This means that one VPN- connection in practice is impossible to hack.
An unencrypted internet connection is basically "open" and it does not actually require the great expertise to monitor it. Unauthorized persons can therefore relatively easily intercept personally sensitive information that can easily be misused. It can e.g. be private content in emails and the like, passwords, credit card information, etc. It sets VPN effectively a stop for using encryption, which makes this data unreadable to outsiders.
Many websites use HTTPS (including of course here too VPNinfo.dk), which is end-to-end encryption between user and web server. However, not all and with an asset VPNconnection, you are always protected against electronic monitoring.
Monitoring in Denmark
It will probably surprise many that all “providers of electronic communications networks and services” in Denmark are subject to Retention Order, which requires “registration and storage of telecommunications data generated or processed in the provider's network”.
In practice, this means that telecommunications companies and internet providers store information about all Danes' use of telephone and internet a year back in time. It's wild - logging on ALL Danes' use of telephone and internet for a year!
The executive order has been declared illegal by the EU, but so far the law is still in force. It also happens not only in Denmark; similar laws exist in many other EU countries.
VPN makes it impossible to register an activity for a user other than connecting to the Internet. The encryption makes it impossible to see what the person has done. Therefore, the log for a person who has used VPN, does not disclose anything about what the person has done online.
VPN hides the IP address and makes you anonymous
Many use VPN to be anonymous so that their movements on the internet cannot be traced back to them. This applies to visited websites, searches, downloaded files, etc.
Uden VPN is one's IP address more or less publicly available and can be "seen" by all websites, websites etc. that one visits.
The anonymization with VPN happens by the user's IP address being hidden when the server acts as an intermediary in the communication between the user's device and the rest of the Internet. This replaces the user's own IP address VPNserver so that it is what other devices on the web “see” when exchanging data.

All devices on the Internet have an IP address that is used in the communication between devices and ensures that the data packets end up in the right places.
IP addresses are managed by ISPs, which have a pool of addresses that are distributed among users' online devices as needed. Therefore, ISPs keep records in its system logs of which IP addresses the users have used at any given time. That way, an IP address can be used to track the person who used it.
You can see the IP address you are using right now with e.g. ExpressVPNs IP tool. Here you will also be able to see the ISP you are connected to the internet with.
With a VPNconnection, attempts to track the user via the IP address will simply reveal the address of the server to which the user has been connected. It can never be connected to the person behind if the provider does not log user data. Therefore, one must choose one
Used one VPNconnection to surf, download, etc., the activity will not be traceable to the user, who is therefore completely anonymous.
Use Google and other sites anonymously
When you use Google, Bing, Yahoo and other search engines, every search you make is recorded and cataloged. They are then linked to your computer's IP address and used to tailor ads and later searches to your device.
This cataloging may seem indifferent and perhaps even useful, but many would like to be in addition if possible. Many have tried to Google something that we would like to keep to ourselves, and then see advertisements for it for weeks after.
With a VPNconnection, the search engine will still register your search, but it will not be connected to your device, as you do not expose your own IP address in public.
An alternative to Google is to use the search engine DuckDuckGowho does not detect and track their users.
Access blocked services and websites
Just as you externally have the same IP address as it VPNserver you are connected to, it will also appear as if you are in the same place as it. All countries use specific ranges of IP addresses that can be used to determine the user's location.
Are you, for example. connected to a server in Germany, you use the network via a German IP address, which makes it look like you are in Germany. It can be used to "cheat" systems that use IP addresses to determine where in the world users are and on that basis may block some content.
In this way, you can access websites, streaming services, TV and Internet radio stations, etc., which are otherwise reserved for users in a specific country.
It is used, for example. to access Netflix USA or the other way, if you would like to see content on DR.dk, but are located abroad. You can only be allowed to do so with a Danish IP address.

Use WiFi hotspots and other open networks securely
Few people think about it, but free WiFi hotspots at Starbucks, McDonald's, at airports, in hotels, etc. are not secure. Public WiFi is not secured with encryption and your data is sent to anyone who is knowledgeable enough to eavesdrop on you.
It's actually pretty easy for an attacker to intercept your unencrypted Wi-Fi signal with one Evil Twin hotspot. Evil Twin is an unauthorized WiFi with the same name as one you might trust is safe to use.
The hacker can e.g. located in an airport where he has set up an open WiFi with an immediately credible name. If you log in to it, you will not notice anything, but because it goes through the hacker's equipment, the connection can be intercepted.

Et trials were carried out at Barcelona airport, where a number of fake hotspots with names like "Starbucks" etc. was established. In just 4 hours, as many as 8 million data packets, including emails, logins and other sensitive information intercepted.
If you log in to a public WiFi and then create one VPNconnection, your data is encrypted and thus cannot be monitored by a hacker. If you regularly travel or use public WiFi, is VPN a good investment in your privacy.
Avoid censorship and use the web freely
At home, we are used to the fact that we largely have free access to everything on the Internet. However, this is far from everywhere and the states of certain nations carry out oppressive internet censorship of its inhabitants.
Iran, Egypt, Afghanistan, China, Cuba, Saudi Arabia, Syria and Belarus are examples of countries where the state monitors and restricts citizens' Internet access.

You can not use Google freely here and it is also blocked for Facebook, Youtube, Twitter and other social media etc ..
In addition to restrictions on Internet access, these countries must also be monitored. In many places, the state largely follows what citizens do online.
VPN is outright illegal in many of these countries, which tells something about how effective the technology is.
If you are in a country where access to the network is limited, you can circumvent the censorship by using VPN. By connecting to a server in another country where no censorship is exercised, one can use the network freely and without restrictions.
This approach is widely used in the aforementioned countries, where many will not find themselves being oppressed, but will be able to use the Internet without restrictions.
Censorship in Denmark
Even though we have unlimited access to Google, social media, etc., there is actually a form of censorship in Denmark. Occasionally, ISPs are required to block websites that are found to be illegal.
In the same way as VPN makes it possible to circumvent censorship in oppressed nations, it can also be used to gain access to blocked websites in Denmark.
Supervision and censorship of jobs and studies
It is not just the state that limits and monitors what people do online. In a company, at an educational institution or the like, there is often a policy for acceptable use on the network.
What this means can be interpreted in many ways and in a number of places quite drastic restrictions have been introduced. It can, for example, be blocking social media such as Facebook, YouTube and Twitter or blocking email services such as Gmail, Hotmail, etc. Often the use of P2P file sharing will also have been blocked on that type of network.
That it is possible to limit people's use of the network in this way is due to the use of the place's local network. This makes it easy for system administrators to block websites, services, etc.
En VPNconnection creates a "tunnel" out of the restrictive network and allows you to connect to websites internet services that would otherwise be blocked for
On a local network it is also easy to keep up with what the users are doing, but here comes VPN again to the rescue. Encryption prevents systems and people from monitoring anything.
In principle, one should respect policies on acceptable use - and of course follow the law. But if you have a legitimate need to circumvent restrictions on a network, one will VPNconnection could help you.
VPN does not protect against everything!
VPN only encrypts the connection between the user and the server. The data flow between the server and the rest of the internet is NOT encrypted and can therefore be well monitored.
In addition, protects VPN not against “social hacking”, phishing, viruses, malware, ransomware, etc. So you still should not respond to emails from alleged African princes and the like.
Whether one uses VPN or not, one should always use the net with care! If anything is scary or too good to be true, then it sure is!

May there be disadvantages to using VPN?
VPN may immediately sound like a digital Swiss Army knife that solves all sorts of problems online. That is to some extent true; VPN is a great tool in many situations, but it can actually cause problems once in a while.
Blocking of VPN
You can sometimes find that websites, web services or the like are blocked VPNusers. In that situation, you will find that the content is not loaded and often you will also receive a message that you are blocked from using VPN or proxy.
Technically, this is done by blocking access to IP addresses that are known to be used by VPNservices. Another method is to analyze data packets that can reveal that one is using VPN.
The problem can sometimes be circumvented by switching VPNserver, because not all related IP addresses are blocked. If that does not work, you have to strike VPN from to access.
Block on online banking
A typical case is online banking, which often does not allow the use of VPN to minimize the risk of fraud. It is quite understandable and sensible both for the sake of the bank and the customers.
If you experience being blocked from your online banking, you must therefore deactivate VPNconnection, to access. In terms of security, it is not problematic, because online banks already encrypt the connection with HTTPS, so here you do not have to fear being hacked.
Blocking of streaming services
Another well-known case is where VPNusers experience being blocked from using streaming services. As a rule, in that situation you will be greeted with a message that you will be blocked from using VPN or proxy.
Streaming services often block IP addresses that they believe are being used by VPNservices. Therefore, it may be worth the effort to switch VPNserver and try again.
Lower download speed and slower response times
With an active VPNconnection, all identical data is passed through VPNserver. All other things being equal, it will result in lower download and upload speeds as well as longer response times, which can make the server a bottleneck.
The reason for the problem is that one makes the distance to the destination “longer” and moreover has VPNservers limited resources allocated to each user. However, many will probably not experience a loss in performance at all, as with most services you can download at up to 300 Mbit / s.
For general use such as surfing, streaming, download, etc. most people will probably find that the benefit loss is minimal and acceptable in relation to the benefits of using VPN. It is e.g. completely unproblematic to stream in 4K / UHD and by ordinary surfing, on social media etc. one should not notice any difference at all.
Gamers will probably not accept the longer response times, so for them there is probably nothing to do but hit VPN from.
Local network issues
VPN gives problems connecting to other devices on local area network. A typical problem is that you can not connect to a printer or the like.
The reason for the problem is that due to the connection to VPNthe server through which all data passes is in practice not connected to the local network. Therefore, you can not connect to devices on the network.
With some VPNservices can be used split tunneling, where you define which data should go through the server. That way, one can achieve the best of both worlds and both use VPN as well as having access to the local network.
Another solution, of course, is just to strike VPN from when to print.
Which one VPNservice is best?
To name the best VPNservice is a bit like finding the best car; it largely depends on your needs. Basically, one should VPNservice however be secure, anonymous, fast, easy to use and have servers where you need it.
In addition, the services often offer a number of additional functions, which are of more or less secondary importance. In some cases, however, these features may improve both the safety and usability of the product.
The price must of course fit the budget and you often get what you pay for. However, a good need VPN not be expensive and several of the best services are actually among the cheapest!
Most services are now really good, but there are a number of technical conditions and conditions they should meet. There are a sea of services to choose from, so there is absolutely no need to compromise on security or privacy.
The main parameters to choose VPN based on are:
- Is secure encryption used?
- Privacy and anonymity on the web
- server Locations
- Network Speed
- additional Features
- Other things worth considering
- Prices and subscriptions
VPN anmeldelser
On VPNinfo.dk is reviewed and reported selected VPNservices on an ongoing basis on the basis of security, privacy, server locations, user-friendliness, extra functions, speed, etc.
You will find the 5 best reviewed services in the table below:
Top 5 VPN services
provider | Score | Price (from) | Review | website |
10/10 | Kr. 47 / md | |||
10/10 | Kr. 42 / md
| |||
9,8/10 | Kr. 44 / md
| |||
9,7/10 | Kr. 35 / md
| |||
9,7/10 | Kr. 36 / md
|
VPNinfo.dk has affiliate agreements with several of the notified providers. If you follow links to the services' websites and pay for a subscription, you will receive VPNinfo.dk therefore a commission for the referral.
However, it does not affect the subscription price or the outcome of the reviews. I always try to be neutral and evaluate the services based on objective criteria. However, certain aspects such as usability will always be a matter of taste.
Secure encryption
The security lies in the encryption that makes your data unreadable to unauthorized persons. Encryption means that your data is re-encrypted with a secret encryption key, which is only yours VPNclient (the program on your computer, smartphone, etc.) and VPNthe server (the computer you are connected to the rest of the network through) has.
Only by having this key is it possible to decode the data stream, which is the whole core of VPN. Therefore, it is extremely important that the encryption is strong.
Encryption protocols
The encryption protocol is the technology used to encode data and achieve a secure connection between user and VPNservice. One can rightly say that the encryption protocol is the "brain" of VPN.
Each protocol has its advantages and disadvantages, but in general they are very secure. They all use advanced mathematics to encrypt data, which in practice is impossible to break. Even with supercomputers, it takes billions of years to break standard 256-bit encryption used by most services.

The weaknesses of some of the protocols are for ordinary people more or less theoretical. They do not lie in the encryption itself (mathematics), but in the way it is implemented in the protocol. It may contain security holes or vulnerabilities that can be exploited.
There are e.g. reports that NSA routinely decodes data encrypted with PPTP and L2TP via backdoors in the protocols that have been compromised and weakened.
Whether it is relevant to you is a personal question. Do you use VPN for streaming, gaming or the like, you are hardly in the spotlight of the intelligence services.
Choose a service that uses open source encryption
It is recommended to use one open source protocol as it provides the greatest security and anonymity. At the same time, there is no downside to it, so you might as well do it.
Open source means that the source code of the protocol is publicly available and therefore can be reviewed by anyone who understands it. It provides a huge amount of security against errors and the like as lots of professionals have reviewed the program. If the code contains errors, security holes, etc., they are quickly found and corrected.
Open source does NOT mean that anyone and everyone can go in and change the code of a program and thus build in viruses, Trojan horses and other dirt. This solely means that the code is open for all to see, which provides a great security against just malicious code.
VPNFortunately, services make extensive use of open source protocols such as OpenVPN and WireGuard. Here, WireGuard can be highlighted as the source code is very short, making it easy to go after in the seams. It is also not very resource intensive and can be used on all devices. WireGuard is “the new thing” and many of the leading services have recently started using it.

PPTP
The point-to-point tunneling protocol is one of the oldest encryption protocols and it therefore works on most, if not all platforms. However, the method is not completely bulletproof and has a security hole that has gotten Microsoft to discourage, that one uses PPTP. A plus of PPTP is that it is not resource intensive, which means it is fast.
L2TP and L2TP / IPsec
L2TP means Layer 2 Tunnel Protocol and as the name suggests, data is encrypted twice twice for increased security. However, it makes L2TP resource-consuming and is therefore considered relatively slow. The protocol may potentially cause network problems and the use of it may therefore require advanced network settings.
OpenVPN
OpenVPN has been given that name since the protocol is open source. It does not appear that the protocol can be broken by the NSA, which can be attributed to the openness that is in open source. In addition, OpenVPN be difficult to block.
Although OpenVPN is open source, the source code is huge. This makes it a big task to follow the program in the seams, which is a weakness.
Another disadvantage of OpenVPN is a lack of support for mobile devices, which, however, is constantly improving.
SSTP
The Secure Socket Tunneling Protocol has the advantage that it is almost impossible to block, thus it is a good choice if the purpose of VPNthe connection is to break censorship. In China, Iran, etc. the authorities are trying to prevent the use of VPN by blocking their access to the network through state-controlled ISPs.
SSTP is considered very secure and there are no reports that it should have been compromised. However, the source code is closed and therefore can not be reviewed by anyone other than the owner and developer: Microsoft.
IKEv2
IKEv2 or IKEv2 / IPsec is not a standalone encryption protocol, but part of IPsec. It is often used in Mac OS and iOS apps, where other protocols can be cumbersome to implement.
IKEv2 is in principle not open source, as it was developed in a collaboration between Microsoft and Cisco. However, there are open source versions.
IKEv2 uses fewer resources than OpenVPN and should therefore be a little faster.
wire guard
wire guard is a new open source encryption protocol designed to be secure, easy to revise and fast. WireGuard is immediately unconditionally the best encryption protocol and for the same reason, most VPNservices recently started implementing it.
The source code for WireGuard is incredibly compact, making the open source code easy to browse. Therefore, one can safely assume that it does not hide weaknesses or gaps as they would be quickly discovered.
WireGuard is "lightweight" and uses a minimum of RAM and CPU. Therefore, it is fast as it does not spend as many resources on either server or in apps. This is especially good news for those who use VPN on mobile devices, which usually drains the battery quickly. WireGuard should not do that.
Privacy and anonymity on the web
An anonymous VPNservice protects its users from tracking. In practice, this can be translated into not storing sensitive data about users.
With sensitive data is meant here information about what the users have done while they have been connected to the service. It can be visited websites, downloaded files, etc.
Protection against tracking via the IP address
When using VPN, one's own IP address is hidden from the outside world. Unauthorized persons can only "see" the IP address of the server to which they are connected.
It protects against tracking via the IP address, which is otherwise a common way to identify people on the Internet. This is done by the ISP passing on information about a customer who has used a given IP address at a specific time.

When attempting to track down a person who uses / has used VPN, the track will end at the server. If the service does not store sensitive data about users' use of the service, it will not be able to pass on information that can be used to track the user.
If anonymity is important to you, you should therefore be aware of whether VPNThe service logs sensitive data about its users.
Select a no-log VPN
Providers are well aware that users value anonymity. Therefore, it is now most common that they do not log sensitive data.
It has the simple consequence that even if they were to feel like it or were forced to hand over sensitive data, there would be nothing to come after. You can not hand over something you do not have.
There is no benefit to the user in data logging, so the guideline is completely clear: Select a provider that does not log or monitor some users at all. By now, not many of them do. So there is no good reason to consider using them at all, logs user data.
Go for one VPNservice registered in a country where there are no legal logging requirements. It could, for example. be a US service, but there are good anonymous providers in many other countries.
Avoid Danish VPNservices
For many Danes, it is obvious to look for a Danish product, but it must be strongly discouraged due to the so-called Logging Directive, which, cf. section 1, requires providers to log data about users:
§ 1. Suppliers of electronic communications networks or services to end users must record and store information on telecommunications generated or processed in the provider's network so that this information could be used as part of the investigation and prosecution of criminal offenses.
There are lots of anonymous VPNservices with servers in Denmark, so there is no reason to prefer a Danish provider for that reason.
server Locations
By server locations is meant the countries, territories or cities where the service has servers that users can connect to.
The need for server locations is individual and depends on what one uses VPN to. A service with servers in all of the world's approx. 200 countries would be optimal, but smaller ones can usually do it.

If you want to bypass blocking and, for example, watch live TV in the UK, you should make sure that the provider has servers in the UK. Do you want to access American Netflix, so you need to connect to a server in the US and it has most services (if not all of them).
Danish servers
For Danish users, there can be two good reasons to go for a provider, servers in Denmark:
- To be able to access DR.dk and a number of other Danish streaming services, the visitor must have a Danish IP address. If you are abroad and would like to use DR.dk or other Danish sites, with visitor restriction, you can only access via a server in Denmark.
- Connection to a server in Denmark provides the smallest delay and highest speed, as the data flow must be "around" the server both to and from the client. Here geographical distance plays a big role and therefore the server should be as close as possible. Alternatively, servers located in Sweden, Norway or Germany can be used, as the distance to this is also relatively short.
Many services have servers in Denmark, but not all, so check immediately if you have the need.
Network Speed
By passing all your data through VPNconnection, it can easily become a bottleneck that slows down to far below what you pay for with your ISP.
The speed of the connection depends on two things: The speed of VPNthe server's own internet connection as well as the resource consumption on the server. An appropriate number of servers, with the necessary resources in relation to the number of users, is necessary to avoid low speed and long response times.
En VPNservice that saves too much on the hardware will therefore often be experienced as slow and perhaps even with outages.
Many of the services claim to be the fastest in the world, but of course not all of them can be. However, they are usually fast enough for most needs.
One should not expect the maximum benefit of a lightning fast internet connection, but most offer download speeds of up to 300 Mbit. There is plenty for streaming in even 4K, but if you download large files, you should expect it to take longer.
You can join VPN of course do not get a faster internet connection than the one you already have from your internet provider…
Servers close by provide the fastest connection
The highest speed is achieved by connecting to servers that are physically close. The farther away VPNthe server is, the slower the connection. This applies to both download speed and response time (ping / latency).
It can therefore be an advantage to choose a service that has servers in the same country as you are located. In geographically large nations such as the United States or Canada, where there are physically large distances, it is also relevant to take a closer look at which cities exist. VPNservers in.
In Denmark, you therefore get the fastest connection by connecting to a server in Denmark.
A good place to test its internet connection is speedtest.net.
additional Features
Extra features cover a number of features that can do VPN-connect more securely, more anonymously or otherwise enhance the experience.
DNS leak protection
When you type a URL such as google.com in the browser's address bar, a lookup is made in the Internet's response to a phonebook where the IP address of the URL is located. It is the IP address that tells your browser which website to display. The URL is just a way to make the display of the address nicer and easier to remember.
The register of URLs and IP addresses is called a DNS (Domain Name Server or name server). It is most often preset in the configuration of your internet connection to use your ISP's DNS.
Even if you use it VPN, you may risk making a lookup in the DNS that takes place outside of encryption. This gap in anonymity is called in the technical language for DNS leak. It can be used to associate your own IP address with a visit to a particular website.
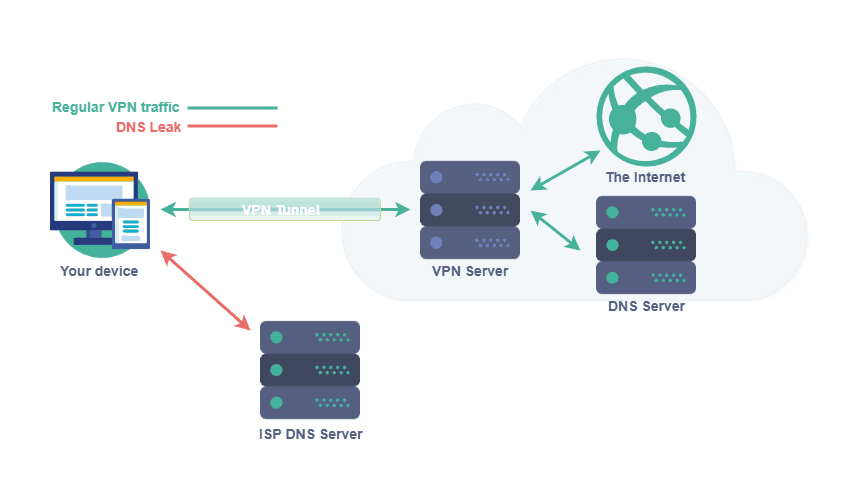
The only information that can be extracted from this is that you have visited that URL. An active VPNlink will still hide what you did on the page. However, many will still find it cross-border to know the ISP can keep up with what they are doing online.
Some services have their own DNS that customers can use. It provides complete anonymity to DNS queries, as you do not use your own ISP's DNS.
Alternatively, one can use Google publicly available DNS servers. Data from users' listings is not stored here either, if you trust Google. However, there is no immediate reason not to do so.
You can on https://www.dnsleaktest.com/ test your connection for DNS leak.
Killswitch or firewall
En kill switch completely blocks the internet connection if VPNthe connection is lost by mistake. It acts as an additional security of the connection, as the kill switch prevents unencrypted data traffic from being exchanged over the Internet. Without a killswitch would interrupt VPNThe connection could otherwise leak sensitive data and compromise the user's IP address.
Kill switch can either be built into the client or use the operating system's own built - in firewall. The latter is the best solution as it completely blocks unencrypted data on a “deeper” level.
VPNconnections are very stable and outages are only rarely experienced, but should this happen anyway, a kill switch is a useful "emergency switch". It is therefore recommended that you choose a service that offers the feature, which most people happily do, but of course also that you make sure that it is activated.
Obfuscation
Obfuscation is a technique used to hide the use of VPN. Although the data stream is encrypted, there are markers that reveal that it is being used VPN. These markers can be found with deep packet inspection, which is a method of analyzing internet traffic.
VPN-the service itself may have developed a variant of an encryption protocol without these markers. Alternately happens obfuscation by adding another layer of encryption on top of already encrypted data. It does not change the strength of the encryption, but simply obscures its use VPN.
Deep packet inspection is used in systems where one does not allow VPNconnections. An example could be with ISPs in countries where VPN is forbidden. Obfuscation is therefore frequently used by users who want to use the internet without restrictions in repressive regimes such as China, Iran, etc.
Many have no need obfuscation and therefore not all ISPs offer it. Do you plan to use VPN in China, Russia, Iran, etc., you should therefore choose a service that offers obfuscation.
Smart DNS
Smart DNS is a technology used to access regionally protected streaming services such as Netflix USA . It basically has not much to do with VPN, but provides some of the same options. Therefore, a few providers have chosen to include Smart DNS in the subscription (e.g. ExpressVPN).
Smart DNS has the advantage that it can be used on basically all devices. Including Smart TV, Xbox, PlayStation, Apple TV, etc., where one can not be installed VPN-client. However, the connection is neither encrypted nor anonymous.
Are you only interested in free access to streaming services regardless of location is Smart DNS an excellent alternative to VPN.
Other things worth considering
Is file sharing (P2P) allowed?
P2P is a type of file sharing where users download files from each other in a network created using dedicated software. It is a very widespread method of file sharing, which is used by both private individuals and a large number of companies.
An advantage of using P2P for companies is that the need for servers to distribute files is reduced by outsourcing the task to the users, who thus help the company by making storage space and bandwidth available. Bittorrent log used e.g. to share the open-source operating system Ubuntu and for updates to miscellaneous Blizzard game.
If you want to be able to use P2P file sharing (BitTorrent) together with VPN, it is essential that it is allowed with the service. This is the case with many - but not all - so be sure to research it before signing up.
How many devices can the subscriber be used on?
In most VPNservices, the subscription can be actively used on several devices simultaneously. In this way you will be able to ensure e.g. his PC and smartphone at the same time.
Since there are typically several devices on the Internet in a household, it is important that the subscription includes sufficient active devices.
In practice, this also means that you can share the subscription with your family and / or friends.
The maximum number of active connections varies between services. IPVanish excels at allowing as many as 10 active units, but the norm is 5-6 units.
Are there apps for all your devices?
One should of course be able to use one VPNservice on all its devices, whatever it is a PC, smartphone, tablet, router, etc.
It is therefore important to make sure that there are apps for Windows, macOS, Linux, Android, iOS and whatever else you need. Fortunately, most have apps for all of the above operating systems.
Do you want to use VPN on your router, make sure that it is also something that the provider supports.
Is the client user-friendly?
VPN is complicated technology, but it must be easy to use and fortunately it usually is too. Most VPNservices have gradually found that apps need to be simple and unmanageable.
As a rule, a simple user interface is used, where you connect to a server with a single click. The image below shows a screenshot from NordVPNs client, which is a pleasure to use.

You can often see screenshots of the clients on the services' website and otherwise you can Google them. Have you already paid for one VPNservice with lousy apps, one can often get the money back for a period and simply try another.
Prices and subscriptions
Price and quality are often linked together and VPN is no exception; here you get (usually) what you pay for.
A major expense for providers is servers that cost both money in procurement and operation. In addition, the cost of Internet connections, which by their nature must be very fast if a high number of users are to be connected without experiencing slow connections.
Therefore, the speed and especially the number of servers is often reflected very directly in the price. If you choose a cheap solution, you must therefore basically settle for a lower number of server locations.
Cheap VPN can easily be the right choice if you do not need specific server locations. Private Internet Access is one of the cheapest secure and anonymous services that keeps the price down with relatively few server locations (35 countries) without compromising on quality.
For how long should you subscribe?
The majority of VPNthe services have subscriptions of different duration. The longer the period, the cheaper the subscription and vice versa.
Short subscriptions provide flexibility
A short subscription is the best in terms of flexibility. If one's needs change, it's smart not to have bound yourself far into the future. Of course, you can just sign up for a new subscription with another provider, but it's a shame to pay too much.
It is also tiring to pay for something you do not use. If one only needs VPN for a short period - e.g. a shorter stay abroad - you can therefore advantageously choose a subscription for a short period.
Long subscriptions are cheapest
Subscriptions for longer periods are cheapest in the long run. There are usually big savings on subscribing for a year rather than paying for a single month at a time.
If there is no prospect of one's needs changing significantly over the next long period of time, a one-year subscription is probably the best solution.
Avoid very long subscriptions
Some providers have subscriptions for extremely long periods of 2 and 3 years. In some cases, lifetime subscriptions are even offered, so you only pay for one time.
That way, they can entice with very attractive prices per month, but it typically requires a relatively large lump sum.
If your needs change, you may have to find another provider within the period you have already paid for. In that case, you may end up not saving anything.
Another possibility is that the service closes and then the money is wasted. The probability of this happening during a so-called lifetime subscription is inherently very high.
Money back guarantee
Most VPNservices offer a money back guarantee, where you can get a full refund for a period of x number of days if the subscription is terminated. It varies a lot how long the period is, but it tends to be 7, 14 or 30 days. CyberGhost takes enough of the record and gives the money back for up to a full 45 days!
The idea is of course to make it easy and without obligation to subscribe and try VPNservice. It's hard to pay for a year if you quickly find out it's a bad product.
In connection with reviews of VPNservices, I have tested the system several times and each time quickly got all the money back, so it's not just empty promises.
Free trial period
It is more normal to give the money back for a period of time than to offer a free trial. However, there are services that can be tried for free for a limited time. There is more about them in the article about free VPN.
Payment Methods
Depending on how big and tight the silver paper hat is, someone would like to avoid paying by credit card and the like. When you do that, you provide sensitive personal information to VPN-The service.
If you use a no-log VPN, there should be nothing to fear, but someone prefers control over trust.
If you belong to that category, you can choose a provider that offers anonymous payment. With some of the services, you can pay with cryptocurrency (Bitcoin, etc.), which is difficult to track.
Some even offer cash payment where you send money in an envelope along with an anonymous customer number.
Available for free VPN?
Of course, there is no need to pay for anything if you can get it for free. However, it costs money to run one VPNservice, so if you do not pay for a subscription, something stays under it.
It can be something as innocent as advertising or a tasting a paid subscription, but the provider of the free service can e.g. also sell sensitive information about your use of the network.
Providers of free VPN are basically inclined to log your activities and show contextual ads when you are connected. They are also more likely to use your user habits to tailor future ads to you, you have fewer servers, and is typically very little committed to protecting your privacy.

After all, they have to make money on something if they run a business. They may offer seemingly fine products (and who wouldn’t want things for free?), But if anonymity and privacy are important to you, it’s best to avoid them.
The providers that cost something usually take your privacy more seriously because you pay for the service. Often they offer a free trial or a free subscription with limited functionality so you can try out the service. Alternatively, free versions with limited functionality and / or advertisements are offered.
Read more about what opportunities are available free VPN.
Get started VPN
Although the technology is complex, it is easy to use VPN. All serious providers offer tailor-made programs / apps to manage the connection as well as simple but detailed user guides.
To start encrypting and protecting your Internet connection, do the following:
1: Select one VPN-service
They are not all equally good, so it does not matter which one you choose. With over 300 services worldwide, there is absolutely no need to compromise! The fundamental requirements are:
- Safety: The ability to protect your data from being intercepted by unauthorized persons. It is done with efficient and secure encryption.
- anonymity: The ability to protect your identity so that nothing can be traced back to you. Here is the main requirement that user data is not saved.
- Features and servers: A good service can be used on all your devices, is easy to use, has servers in the places you need and is fast enough that you do not notice losses in speed.
- Extra features: choose one VPN with the features you need. For example. obfuscation, if it is to be used in China or the like.
2: Install the app (or configure VPN manually)
Once you have subscribed, you will shortly receive an email with instructions on how to use the service on your devices.
Most - if not all - VPNservices offer apps / programs to handle setup and management of VPN compound. For most users, therefore, it is obvious to use this solution rather than looking for alternatives.
The services' own software is adapted and optimized for their system and will therefore usually be both the best and not least easiest way to manage VPNconnection.
They can also have a number of useful features built-in that would not otherwise be usable. It can e.g. be a speed test that scans those available VPNping / latency and download speed servers to find the best / fastest for the user's physical location.
It can also be one killswitchthat only connects to the Internet if there is a connection to one VPN server. This prevents leakage of unencrypted data if there are any outcomes for any reason VPN compound.
Therefore, it is definitely recommended to use the programs and / or apps that VPNthe service offers. They provide the best utilization of the product and ensure optimal user-friendliness.
Once the app is installed, you usually just need to enter your username and password and then you are good to go.
Manual setup
If one insists on not using VPNthe software of the service (or if you have chosen an obscure service that does not offer that kind), you can use them VPNclients built into all popular operating systems and certain routers.
That approach will usually not provide the same options extra features that the services software offers. It certainly will not be easier either. In return, one will be able to use VPN without having to install additional apps or programs, which there should probably be someone who prefers.
You will find general guides for setting up VPN on a number of popular operating systems / devices including.
- Configuration of VPN in Windows (Is on the road)
- Configuration of VPN on Mac (MacOS)
- Configuration of VPN in Android
- Configuration of VPN on iPhone and iPad (iOS)
- Configuration of VPN on ASUS Routers
3: Activate VPNconnection
After that, all that remains is to connect to a server, which is done with a single click in the app. Often one can choose to connect to VPN automatically when the device starts up, so you do not have to mess with it every time you want to go online.
Once the connection is activated, you are ready to use the Internet safely, anonymously and freely!
4 (optional): Test VPNconnection
One does not "notice" immediately that VPN is turned on, so therefore it is obvious to want to test if it now works. Unfortunately, there is no easy way to test the encryption, but there are several ways to test whether you are connected to a VPNserver.
One of the methods is to test with ExpressVPNs IP tool. With an active VPNconnection, the displayed ISP (ISP) should not be the one you are getting internet from. If you are connected to a server in another country, this must also be stated.
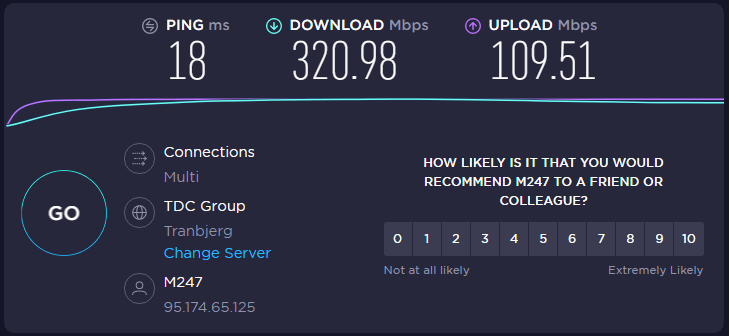
Another way to test the connection is a speed test Speedtest.net. Here, in addition to checking the IP address, you can also see download speed and response time (ping). If you run tests with and without VPN, your IP address will change (red square in the image below). you will also see a name other than your ISP over the IP address (here M247).

Last but not least, you can also use the test on ipleak.net, which in addition to the IP address also shows all sorts of other nerdy information such as your device's operating system, DNS servers, etc.
Top 5 VPN services
provider | Score | Price (from) | Review | website |
10/10 | Kr. 47 / md | |||
10/10 | Kr. 42 / md
| |||
9,8/10 | Kr. 44 / md
| |||
9,7/10 | Kr. 35 / md
| |||
9,7/10 | Kr. 36 / md
|






How to buy this vpn??
Under each review You can go to the provider's website where you can buy VPN.
How do I get out vpn? I can't get on the ebook
You need to open yours VPNclient and disconnecte.
Hellow my name is Martinhaw. Wery capable article! Thx :)
Thanks! :)
Hi
An interesting page you have started up. Nice done. I have a question that you may be able to help with. I do not know if that's something you care about, as you can say.
I'm not a very good user of these systems, therefore my questions. I appreciate all our personal safety and private life. Sadly, there are virtues under pressure at these times, especially thinking of the threat of hackers, but also national states trying to influence society, and thus me too.
To start on the "top" there I have a router Archer C7. A smart TV 2017, two iPad mini and two iPhones. Can these devices run on Express VPN?
We have Netflix, VIAPLAY and HVB Nordic. Can this still run.
We live in Sweden (Vellinge a little north Trelleborg) and would like to see DR1 and TV2 again from their archives, which we can not today. We have Danish Boxer, current programs we can of course see.
Hope you can have time to help.
Summer greetings
Jørgen Albertus
Hello Jørgen
First, thank you for the rose. :)
With regard. your devices, so your iPads and your iPhone can be used properly ExpressVPN And that can your TV in a way too, then ExpressVPN has Smart DNS included in the subscription. When I type “in a way”, it's because you can not encrypt the TV's internet connection, as it can not run a VPN client, but you can join Smart DNS access to e.g. Netflix USA, BBC, DR and Danish Netflix from abroad etc.
You should be able to easily see DR1 and TV2 from abroad if you are connected to one VPN server in DK or use Smart DNS on the television.
Hope it gave you answers?
Hi, I have a similar question
I have Yousee cable tv (intermediate pack) as well as broadband / internet / router same location from with 10 / 10MB connection.
I have a LG smart tv xnumx, portable windows pc, ipad and iphone.
Can I see my Danish TV channels when I go to Spain via Jeres VPN connection.
Thanks in advance for your reply.
Sincerely,
Erik Petersen
VPNinfo.dk does not offer its own VPN, but you should be able to see Danish TV channels from abroad if you connect the device to one VPN server in Denmark.
Hi there
I have several different devices (pc, mac, nas etc.)
If I connect with a simple device, I will then have a garden VPN connection on all devices?
No, you only have VPN on the connected device.
This means that when I have a PC, ipad and iphone I have to buy VPN abonenent to each of them?
No no. Most VPN subscriptions can be used on several devices - also at the same time.
How do I cancel my subscription? VPN 360?
Sincerely. Susanne
You should be able to do that on their website. Otherwise contact their support. :)
How to install VPN on my mobile router (Huawei 4GRouter B525)?
Hi Leif
I don't think you can, but you need to check the router's manual to be safe. The problem is that VPN decryption requires a lot of resources (CPU and RAM), which most routers do not have much of.
Hi Søren
Due to uncertainty and lack of knowledge I have not been installed VPN yet. I am the "nerd" who is best 3mm above the keys on the PC.
I have a follow-up question Is it possible to install VPN on the router (Archer C7) so that my devices, when connected to WI-FI, are automatically connected to VPNserver, or each device must be installed separately.
Best wishes
Jørgen Albertus
Hello Jørgen
You can actually do that. There is a guide here: https://www.wirelesshack.org/how-to-setup-a-tp-link-archer-c7-router-as-a-vpn-for-all-home-devices.html
Excuse the long response time, your question was unfortunately overlooked!
Regards. VPNinfo.dk
How do I extend my subscription?
I'm only interested VPN.
You must do that on yours VPNprovider's website. You must log in to your account and look under subscription, payment options or the like. It varies according to which provider you use.
I have bought and installed PIA on a PC for now. Everything works fine, except when I want to save a file on Onedrive. Then I get feedback that I do not have internet connection and not access to my Microsoft account. I can then beat VPN from, log on to Onedrive and save the file. Seems very cumbersome. Is there another solution?
Microsoft OneDrive blocks some VPNservices and unfortunately you cannot do anything about it.
Roof
When I use one vpn connection, is my mail so encrypted?
The connection to your webmail - e.g. to gmail.com - will be encrypted. To secure the email itself so that it cannot be read by anyone other than you and the recipient, it must be encrypted. It may VPN not clear as it only relates to data on your internet connection. If you use gmail, you can take a closer look this guide.
Are documents I save in Onedrive covered by one VPN connection?
Mvh Line
One activated VPN will also secure your connection to Onedrive. Without knowing the technical details, however, I believe that Onedrive already uses HTTPS, so that connection is already encrypted.
ეს translate- თი ნათარგმნი ტექსტი რა რა უბედურებაა, კარგი კარგი თარგმნე მარა სადამ დადე შენ მაინც წაიკითხე გრამატიკული შეცდომები მაინც გაასწორე თან თან VPNის შესახებაც გაიგებ გაიგებ რამეს შენთვითონ არ გაინტერესებს რა წერია აქ და ვინ წაიკითხავს ამ
Dear visitor
Yes, you have read an automatically translated page and while it'd be optimal if the translation was perfect that's unfortunately seldom the case with auto translations. However, I still believe it is better than having to learn the language the article was originally written in: Danish. Hope you learned something despite of the probably awful translation!
Best regards
Looking at the top 2 items in the list discredits this comparison. If you want a VPN for the sole purpose of appearing to be in another country then these are fine. If you want it for any sense of security then avoid these options as they are the McDonalds fast food of VPNs.
The reviews are based on assumptions of what most use VPNs for and for those purposes the security of the top items in the list is more than adequate. For example, ExpressVPN had their claim of being a no-log service put to the test in a high profile police investigation. Despite gaining physical access to the used servers, the police were unable to find any evidence in the service's logs proving ExpressVPN effectively protects the privacy of their users.
But perhaps you're referring to other aspects of "security"?
Hi, un vpn for android ca sa nu-mi monitorizeze traficul, exista? May concret, date unlimited. Thanks
Hello! Most paid VPN services are anonymous and do not monitor you. They usually also allow unlimited data.